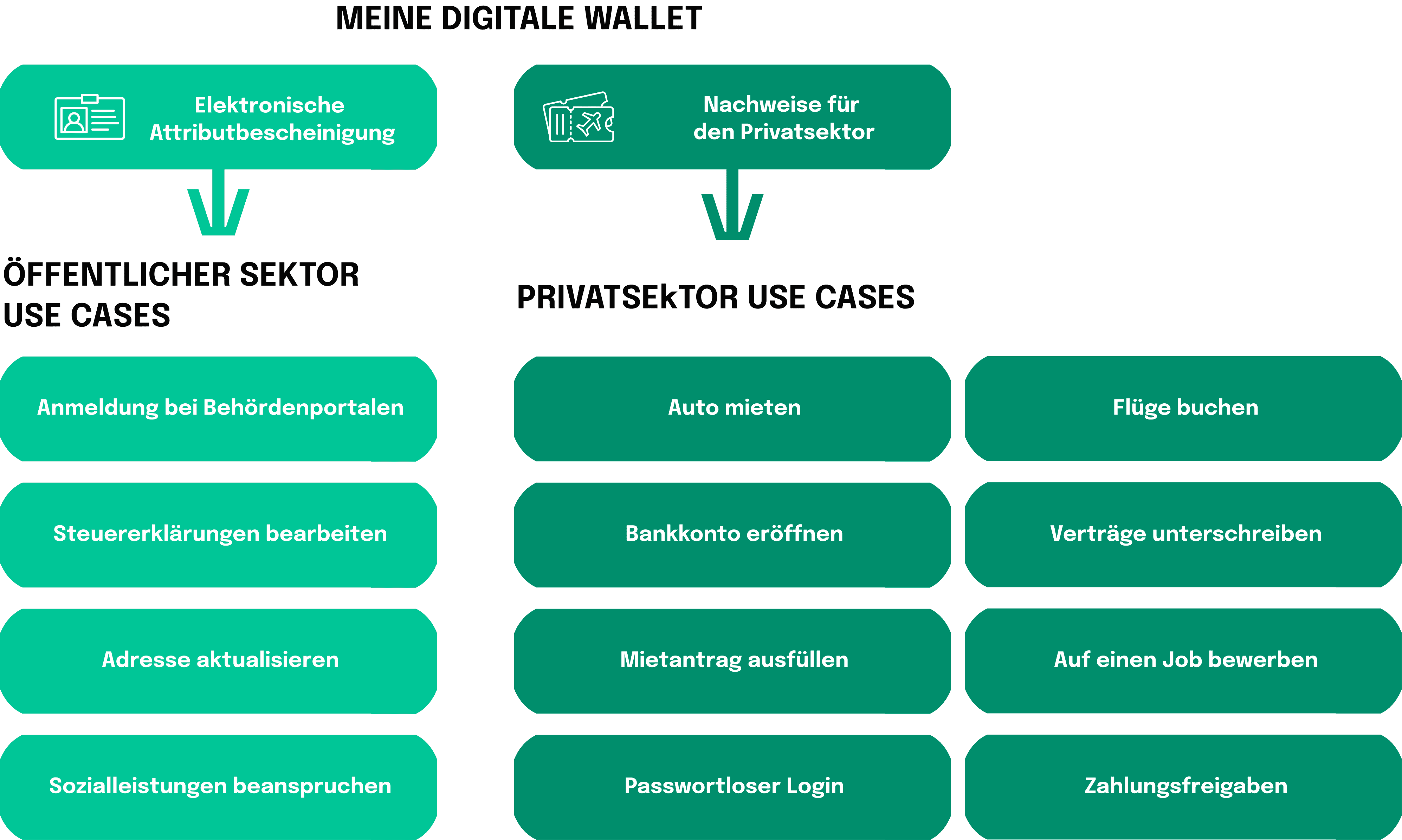
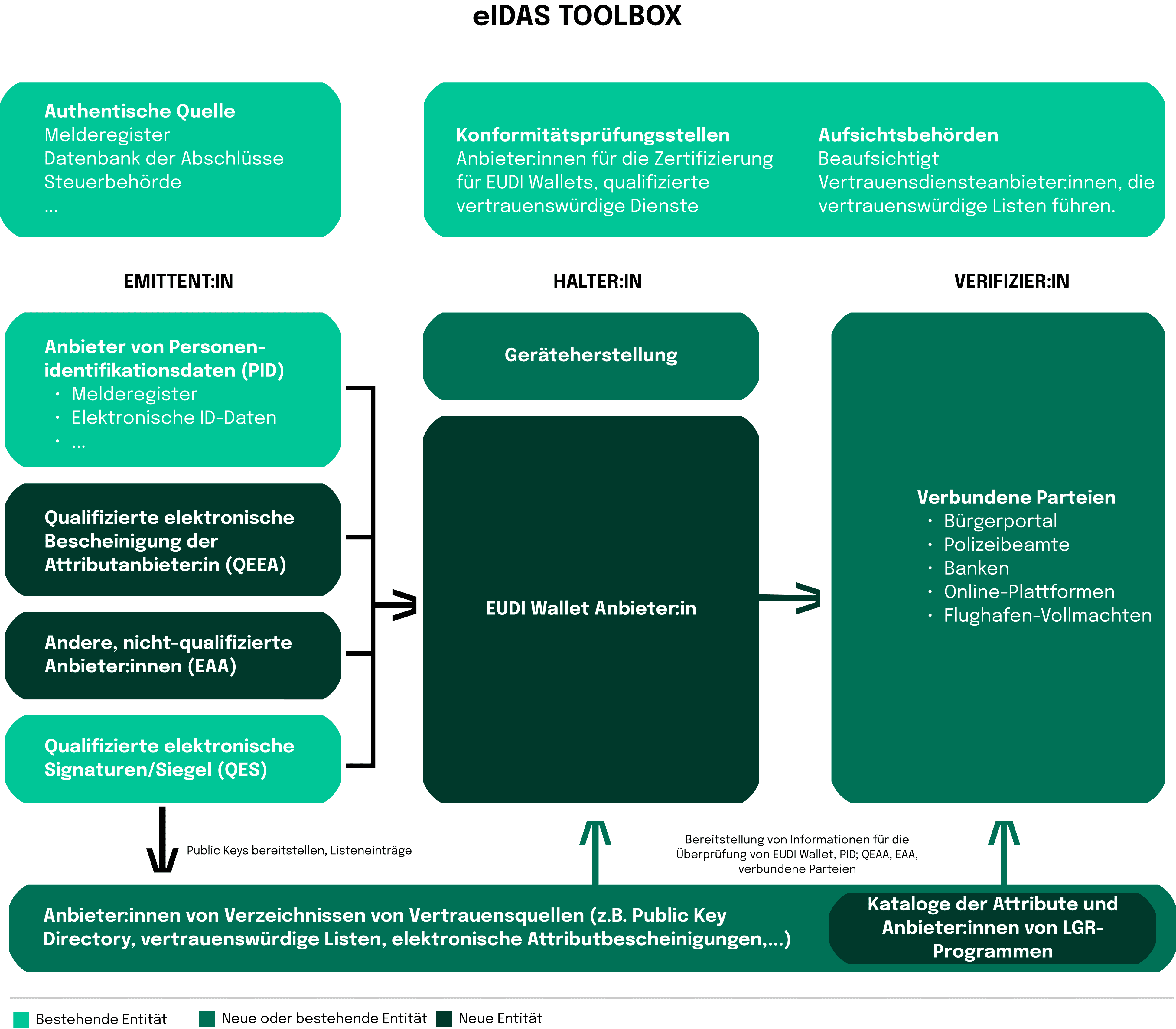
In an age where digital interactions have become the norm, unlocking a secure, efficient, and legally sound way to navigate the online world has never been more critical. The conception of digital identity solutions dates back to the early 2000s, when several European countries started adopting initiatives to facilitate electronic interactions and e-government services. However, those early prototypes were often fragmented and lacked cross-border interoperability, urging the European Commission to eventually consolidate a unified approach to digital identity and trust services. As a result, The “Digital Agenda for Europe” was introduced in 2010, outlining the vision for a single European digital market. Two years later, the first proposal of eIDAS (electronic IDentification, Authentication, and trust Services) regulation was released, aiming to provide a common framework for electronic identification and transactions within the internal market. The revised version of the regulation became fully applicable in 2016 with the member states being required to implement it into their national laws. However, it was not until 2018 that eIDAS was finally extended to include the provisions on electronic identification (eID). While the previously established framework recognized a limited range of electronic documents, such as signatures, seals and time stamps, the expansion allowed for the mutual recognition of national eID schemes across EU member states, enhancing cross-border interoperability.
In practice, the significance of this initiative conveys into implementation of services like DigiD. This particular electronic authentication system used in the Netherlands allows Dutch residents and businesses to securely access various online services provided by government agencies and other organizations from the European Economic Area (EEA) countries. Similarly, SPID, the Public System for Digital Identity in Italy, makes it possible for a citizen to use their username and password to access public services online in the Netherlands, and vice versa.
Aside from an obvious feature of providing the users with a unique digital identity and subsequent access to a range of online government services, such software programs offer an array of key functions. For instance, multi-level assurance allows users to opt for a level of security that fits the requirements of a specific online transaction. The higher the level, the more secure the identification and authentication process. Services such as SPID and DigiD were designed to promote the interoperability of digital identity, ensuring that users can access the platforms seamlessly across European borders. At the same time, user privacy and data protection are also being considered. These useful digital intermediaries strictly comply with relevant regulations to safeguard personal information and digital interactions.
All of these advantages are owed to the eIDAS regulation that has been changed since 2014 and continues to evolve until the present day as digital technologies and practices advance. The key objective behind the regulation is building a seamless and trustworthy digital environment in the EU, supporting e-commerce, e-government, and numerous other online applications. Nonetheless, some would argue that the roll-out of eIDAS as the first pan-European identity scheme has not been wildly successful. Some of the challenges associated with the hindrance in wider implementation include overly complex technical architecture, restricted private sector use, a poor user interface, additionally to a small and inflexible data set.
Fortunately, the recent updates and amendments were made to address emerging challenges and align with new technological developments, as the European Commission published the latest proposal for a revised eIDAS 2.0. The improved regulation is projected to facilitate more widespread acceptance of electronic services across all EU members. Particularly, there has been some reluctance to adopt the use of electronic signatures, especially by financial institutions. Recently, however, there has been a rise in the use of digital signatures with the global eSignature market projected to reach almost 26.6% CAGR over the next nine years, according to Prescient & Strategic Intelligence. Consequently, eIDAS2 has set the objective of increasing the current adoption rate of digital identity services by citizens from 59% to 80% by the year 2030.
Furthermore, the updated regulation also includes additional types of electronic trust services. While the original regulation only applied to e-signatures, electronic seals, and electronic timestamps, eIDAS 2.0 has been expanded to cover e-registered delivery services, e-certificates for authentication, and seals for electronic documents.